If you have password writeback enabled and a user performs self service password reset (SSPR), the user’s new password should be written back to on-premise AD as a non-expired password. That is, after the password is written back to on-premise attribute PwdLastSet should be updated with the timestamp of the password reset:
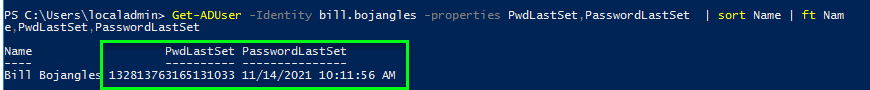
Additionally, the on-prem AD user’s account option flags should not have “User must change password at next logon” flag set:
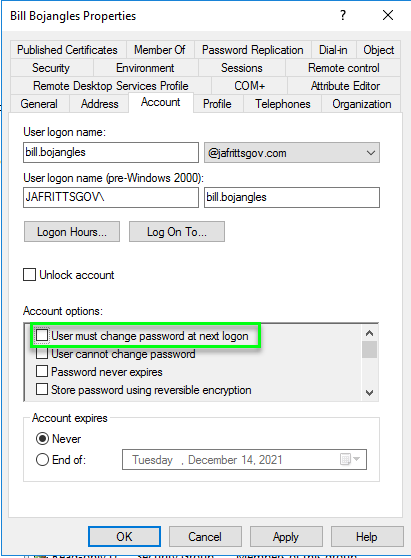
These two factors would indicate the user’s password is not a temporary password that expires but a permanent one as expected.
Why would “User must change password at next logon” flag be enabled after password writeback?
If instead, the above to factors are not true, then something went wrong with the password writeback operation and the password will be considered temporary\expired. This will mean the end user will have to change their password during the next logon to an on-premise AD joined resource. This is not expected behavior.
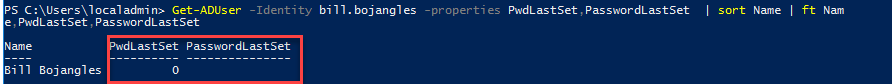
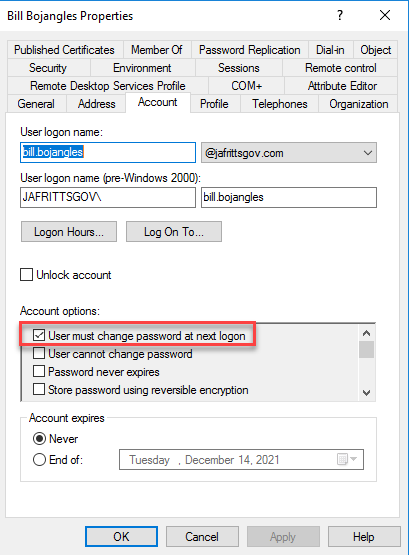
The most common reason is that the Azure AD Connect on-premise AD service account (typically MSOL_b38random9b@domain.com does not have sufficient permissions on the domain to perform “Unexpire password” operation
Most default Windows AD domains will have this permission granted to at the root domain level to all “Authenticated Users” and so MSOL service account will have this permission as well :
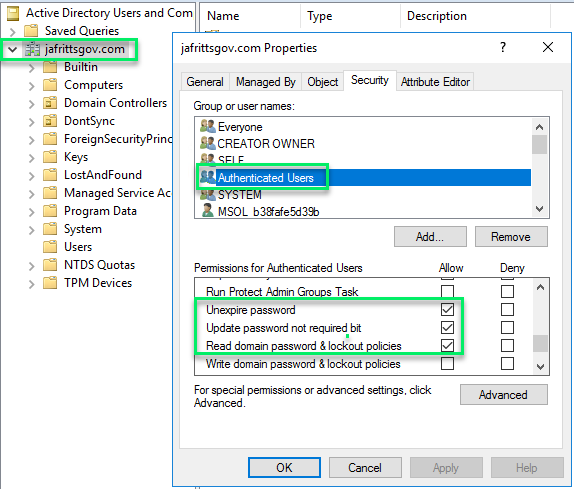
However, I have seen a number of scenarios where for security reasons this permission might not be granted to all users. If this is the case, you will want to ensure you grant the MSOL service account this permission manually to root domain and all descendant objects:
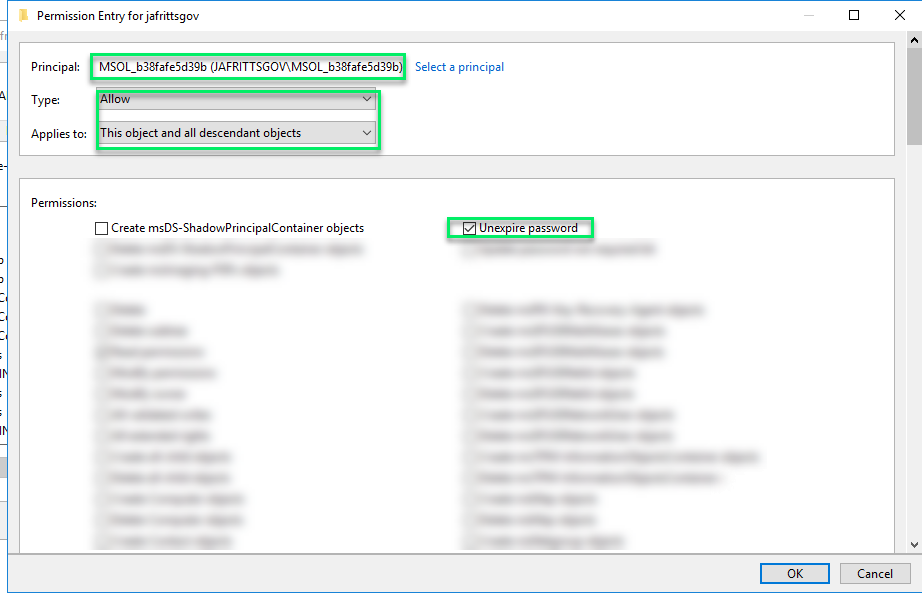
Once this is applied, you should be able to have the user reset their password via SSPR and the password writeback operation will not set the “User must change password at next logon” flag as it will set the PwdLastSet timestamp succesfully.
Note if there are any other permission related errors, follow the Enable password writeback to on-premises \ Configure account permission for Azure AD Connect public doc for all of the permissions required.
Another quick note that has caused some confusion…
If instead of the end user performing SSPR from https://aka.ms/sspr the AAD admin is resetting the user’s password on the user’s behalf from the Azure AD portal -> User Profile -> Reset Password link.
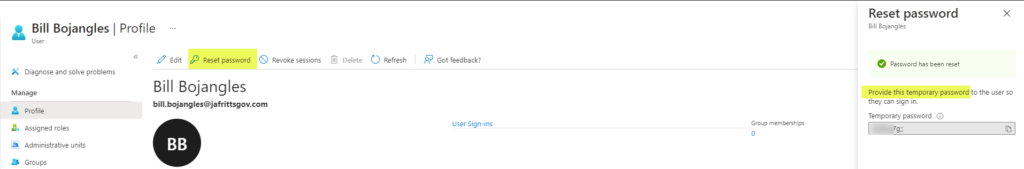
Then it is by design \ expected for the on-premise “User must change password at next logon” flag to be selected during the password writeback operation. This is because admin initiated password reset only sets a temporary password not a permanent one.
This fact is explained in https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/active-directory-users-reset-password-azure-portal#to-reset-a-password but is also mentioned in the Azure AD portal’s dialog during the reset password operation